This lab’s two-factor authentication is vulnerable to brute-forcing. You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code. To solve the lab, brute-force the 2FA code and access Carlos’s account page.
Victim’s credentials: carlos:montoya
Lab: 2FA bypass using a brute-force attack
- First we will login by the username and password
- Here if we give 2 wrong OTP we are logout.
- Go to settings > sessions > add
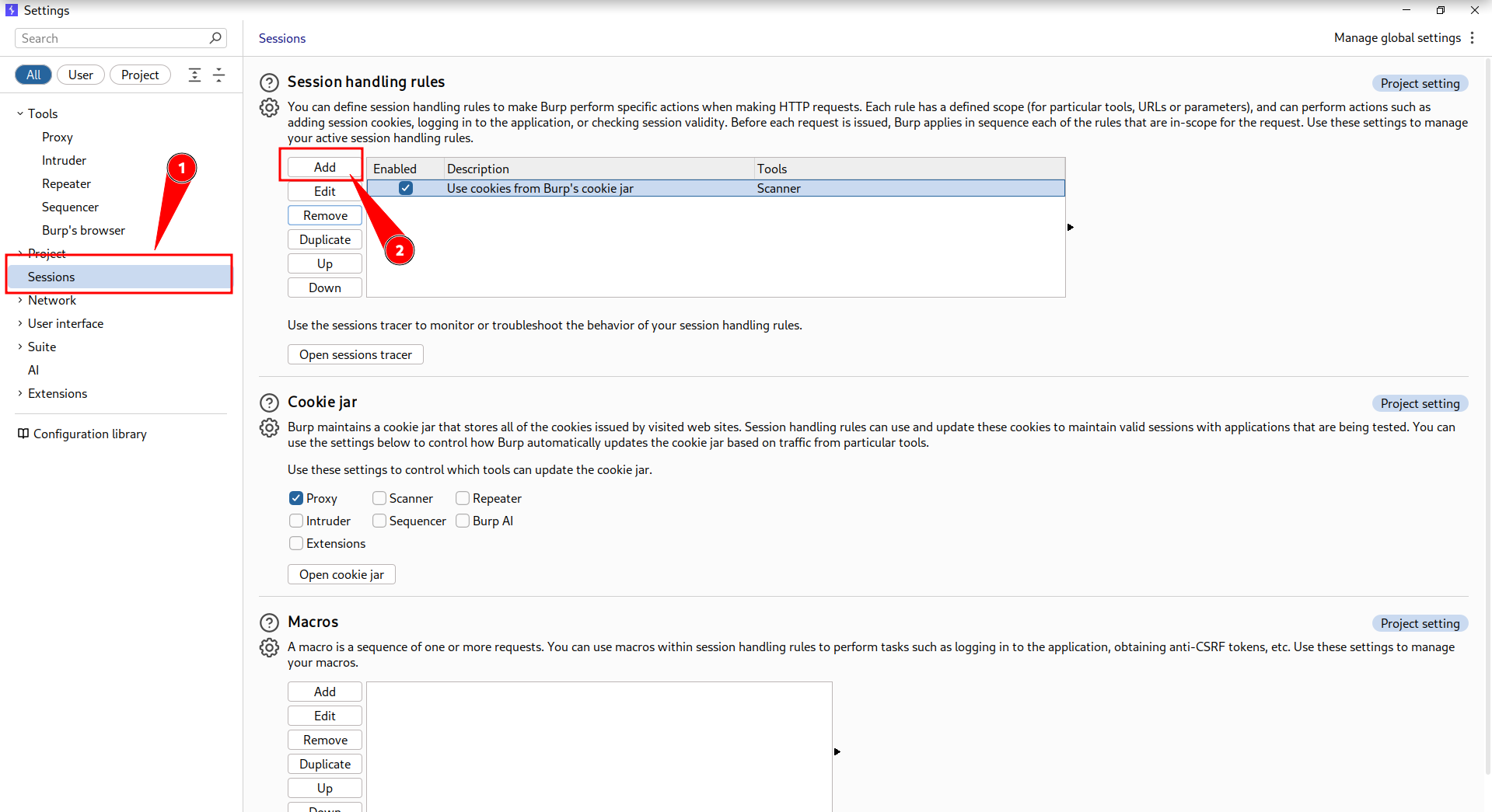
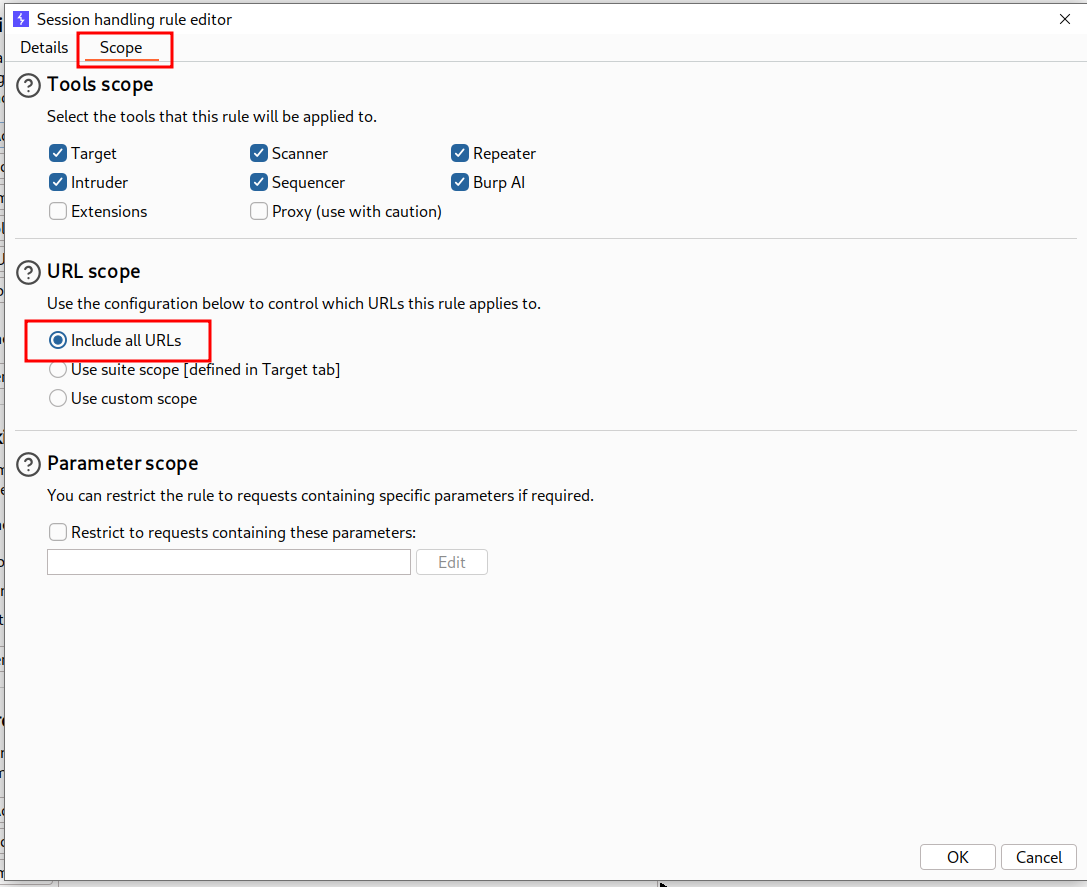
- In scope include all urls
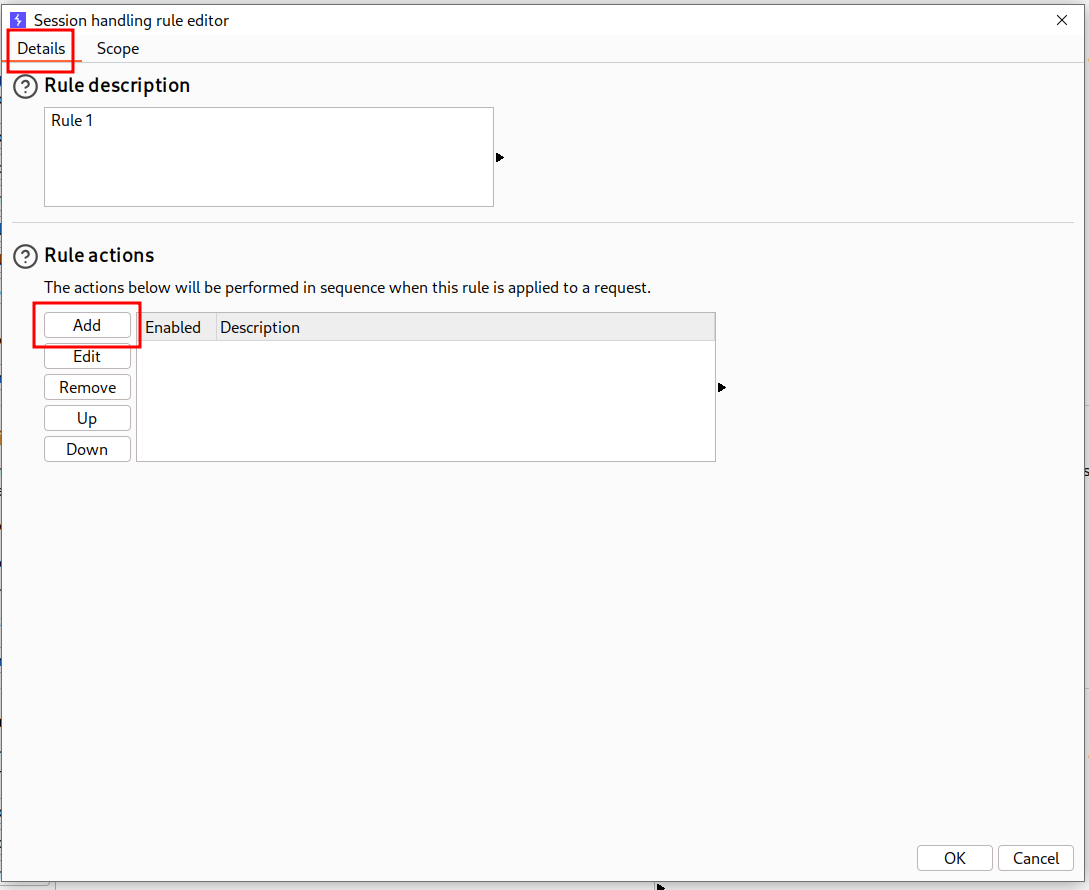
- In Details add > run a macro
- Then select add
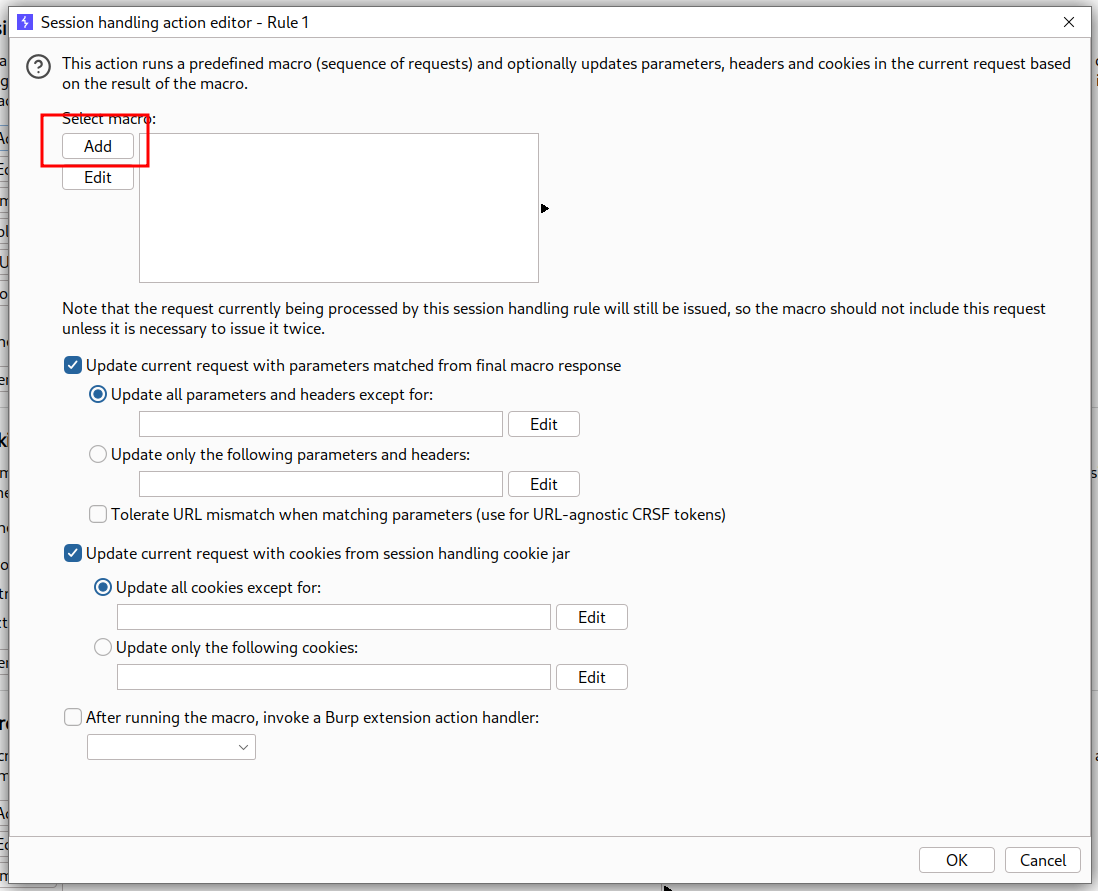
- Select the requests you want
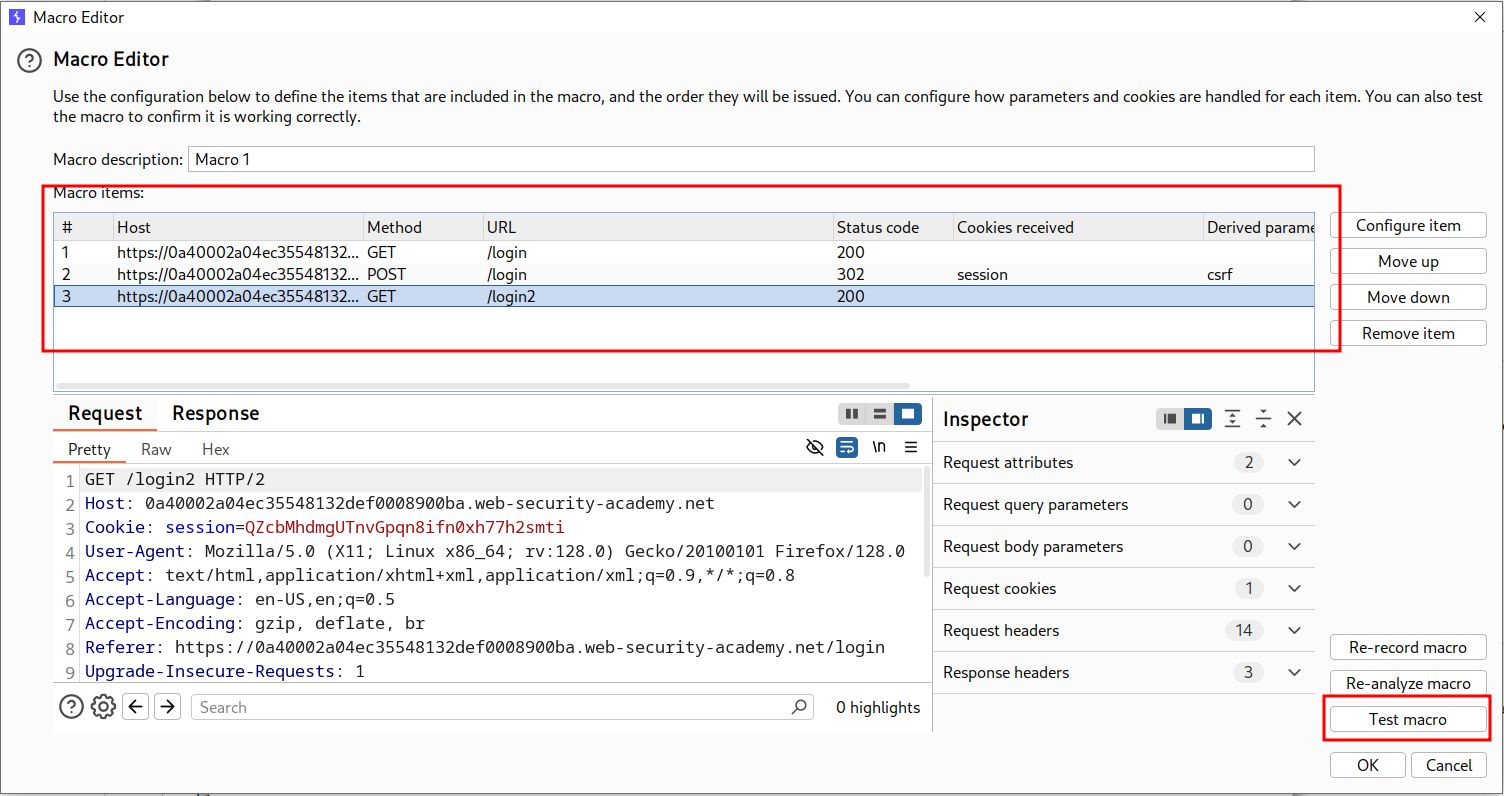
- If all OK then pick the /login2 request with the request we will send brute force the OTP
- We will try 0000 to 9999 and we will send the request at a time.
- When you get status code 302 copy the session code and replace the link in browser.